Active Directory Audit
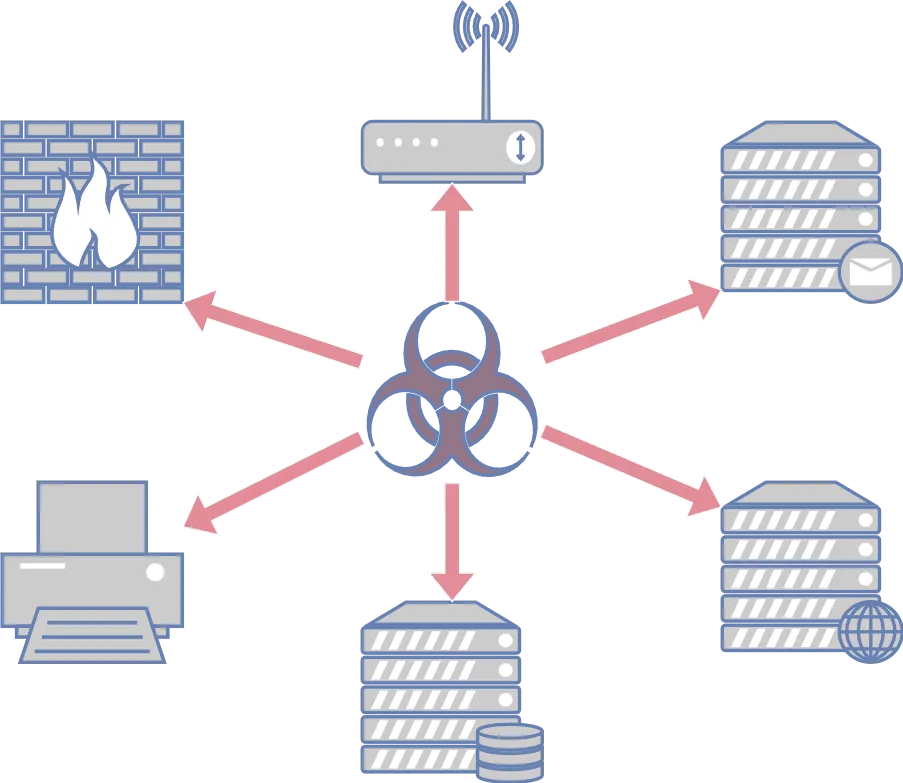
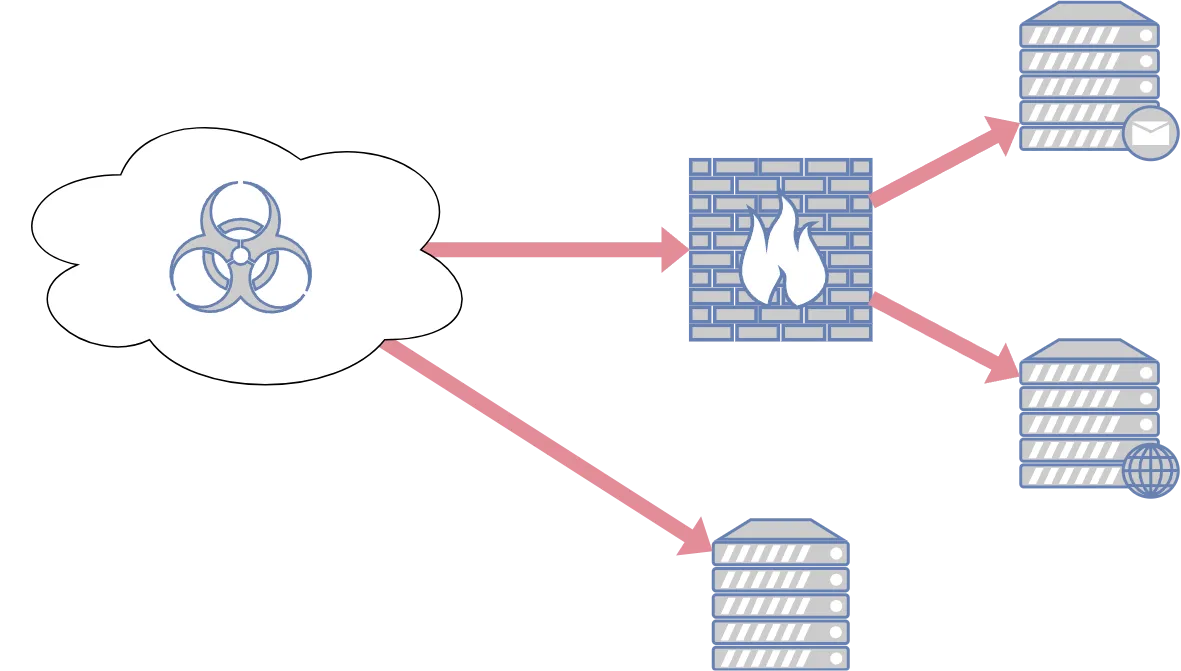
Ransomware attacks are on the rise, and the ones with the highest impact take over the whole Active Directory. We must secure these systems to minimize the risk of having our data encrypted and put up for sale on the internet!
Active Directory deliver extensive functionality; however, their complexity can often lead to security vulnerabilities. Given the critical role these systems play in user management, any security flaws can have severe implications. It is important to note that even though Active Directory serve similar purposes, the systems are still very different and would normally be tested in two different projects.
VidraSec offers services designed to address these challenges head-on. Together, we will develop strategies to fortify your environment against threats.
Scope
This type of test is typically performed as white-box, meaning that the testers receive full access to the tested system and its documentation. This allows a comprehensive analysis of vulnerabilities and misconfigurations in a short time frame. These are the main focus points of the test:
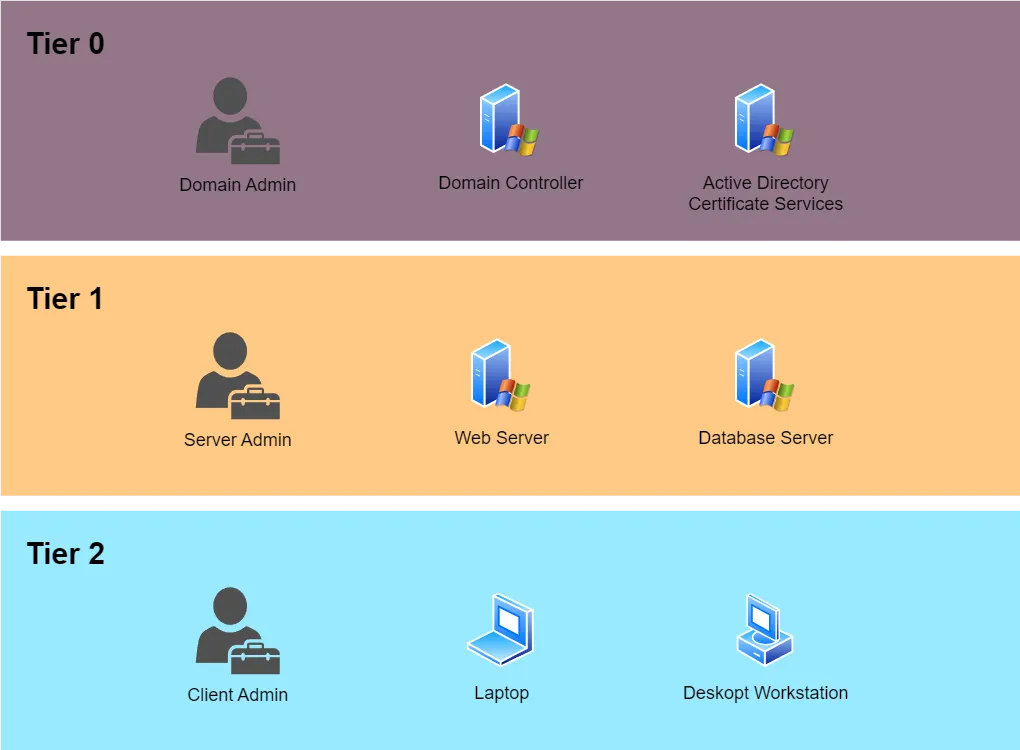
- Audit of the implementation status of the tier model and possible vulnerabilities
- Review of all accounts and their password age
- Review of the permissions of users, computers, and groups
- Review of group memberships of highly privileged groups
- Interview with administrators on how they typically administer the system
- If present: domain and forest trusts
- Test for typical vulnerabilities like “Kerberoasting” or (un)constrained delegation
Why
- Forgotten, insecure permissions can be a huge security problem, making attacks extremely easy.
- These are living systems, and errors occur. Only a regular check can help find them.
- Having secure administrative processes makes the lives of the attackers very hard.
For a comprehensive assessment of the on-premise Active Directory, VidraSec recommends conducting this analysis in conjunction with a penetration test of the internal infrastructure. This approach offers a complete overview of your internal systems’ security posture.
Why VidraSec 🦦
I have multiple years of experience attacking and securing Active Directory. If I manage to get Domain Admin permissions after a few days of work, I am sure a real attacker can also do it. Thus, let me demonstrate what is wrong and how to fix it to protect yourself against attacks.
Typical Price
from 8,400 €
The final price depends on the scope of the project and the maturity level of your IT security. It is calculated individually based on the required effort.
|
martin@vidrasec.com |
+43 670 3081275 |
+43 670 3081275 |
Book appointment |