Dump Hashes in Windows 11 24H2
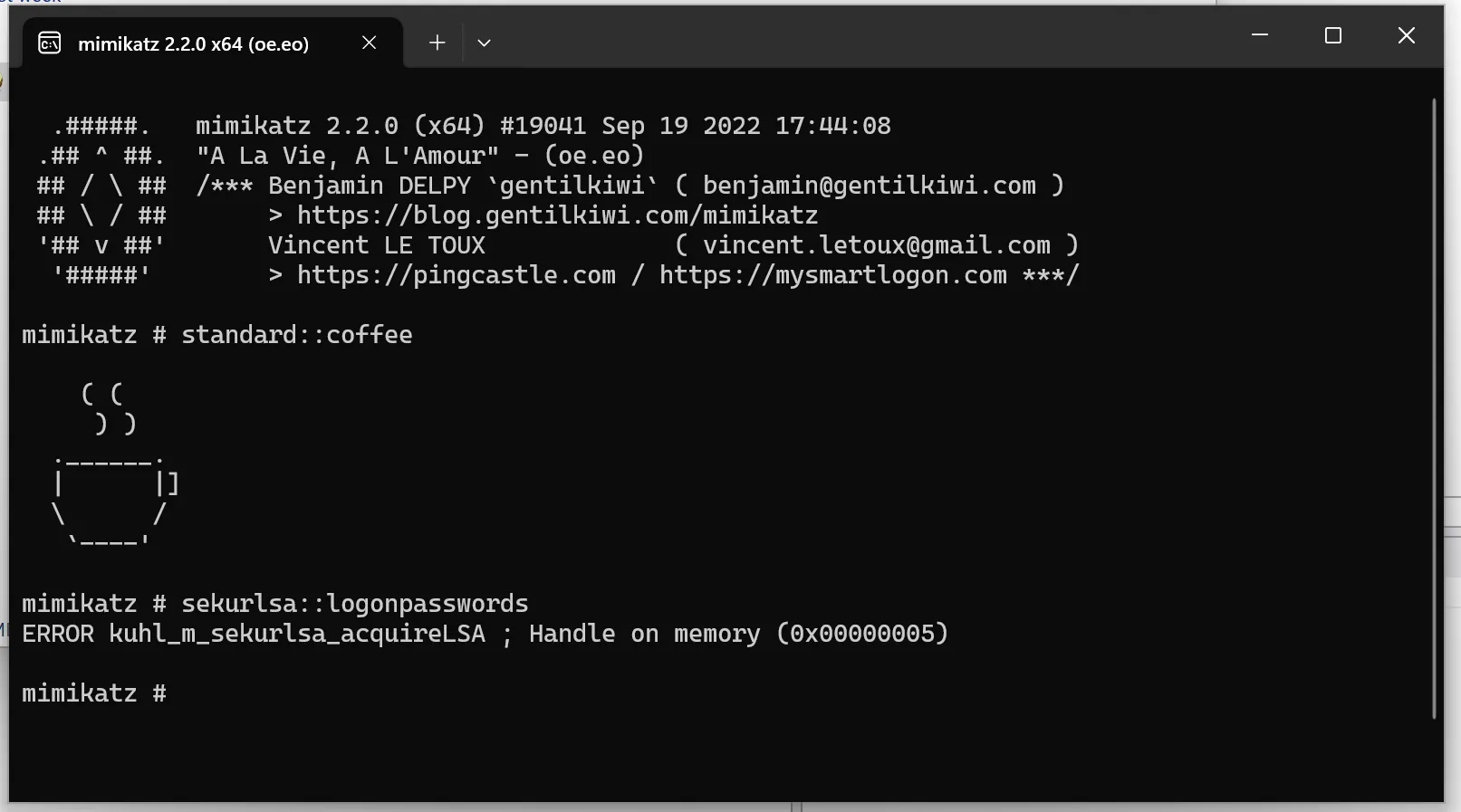
In this blog post, I describe how I managed to read password hashes from the lsass.exe process memory in Windows 11 24H2. Since this version was still very new at the time of writing this post, some of the issues are due to a lack of tool support and should be resolved in the future. However, this post may also help in adapting the tools for later Windows versions.