In this blog post, I will briefly address two often overlooked vulnerabilities and misconfigurations in the Active Directory Tiering model. Specifically, I will focus on the mishandling of terminal servers and the helpdesk user group.
Proper Classification of Terminal Servers
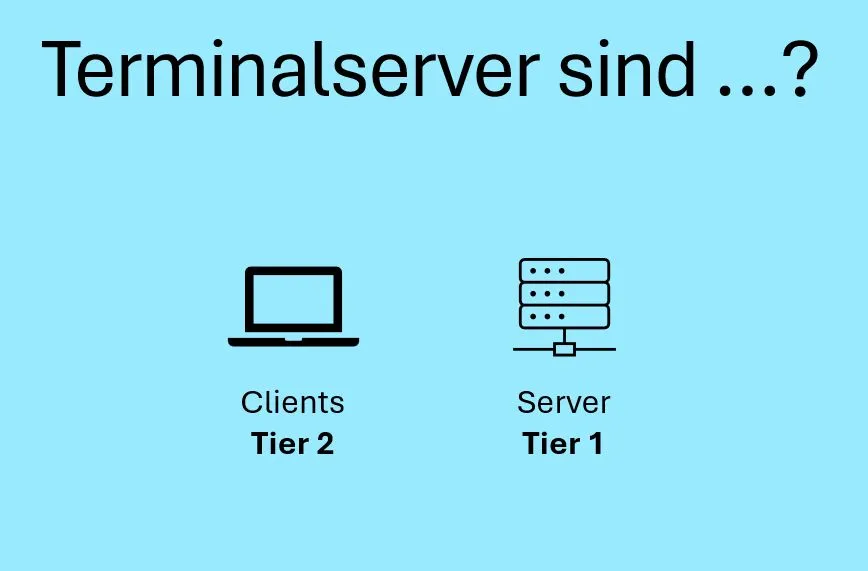
A common misconception in practice concerns the correct classification of terminal servers within the Active Directory Tiering model. Terminal servers, including Citrix systems, allow users to connect to a virtual desktop environment. These systems are often mistakenly classified as Tier 1, simply because they are servers.
Why Terminal Servers Belong in Tier 2
From a tiering perspective, terminal servers are clients, as regular users log in there. A compromised user account poses a significant threat, as attackers can gain access through a successful phishing attack or another attack method.
Once an attacker has access, they only need to exploit a Privilege Escalation—new vulnerabilities in this area are continuously discovered and published. If successful, the attacker can work as a local administrator on the terminal server and compromise logged-in accounts. If a Tier 1 administrator is among them, the entire security structure is at risk.
Conclusion
➡ Terminal servers must be considered as clients and therefore belong in Tier 2!
This misconfiguration regularly occurs during penetration tests and has played a decisive role in achieving Domain Admin status in the past. The tier model is an effective protective measure, but only if it is consistently and thoughtfully implemented.
Securing Helpdesk Rights
In many companies, alongside administrators, there is a Helpdesk responsible for various tasks, including resetting passwords or fixing client issues. Typically, helpdesk employees do not have direct access to servers, and therefore are assigned to Tier 2.
Critical Misconfigurations in the Helpdesk Area
There are two fundamental configuration mistakes that companies typically overlook in order to prevent uncontrolled privilege escalation:
- Can the Helpdesk reset a Domain Administrator’s password?
- Can the Helpdesk perform administrative tasks on a Domain Administrator’s client machine?
If these questions cannot be clearly answered with No, there is a risk that an attacker may gain access to higher privileged accounts through the helpdesk and undermine the entire security model.
A Often Overlooked Danger
A less obvious but equally critical risk exists in the possibility that the helpdesk can reset the passwords of executives:
- Can the Helpdesk reset the CEO’s or CFO’s password?
Although this point is often ignored, a CFO’s account is often more valuable to attackers than a Domain Administrator’s account. Financial transactions, business communication, and confidential documents are attractive targets for attacks.
➡ An attacker doesn’t need ransomware if they have direct access to the company’s bank account.
Testing the Tier Model in Practice
The Tier Model is a central security measure to make attacks within a corporate network more difficult. However, it can only fully protect if it is regularly reviewed and tested.
Have you already tested your Active Directory?
Only through targeted security reviews and penetration tests can the actual risk be assessed and potential vulnerabilities closed in time.
Contact VidraSec now for more information!
|
+43 720 971425 |
martin@vidrasec.com |
Book appointment |