Firstly, what exactly is BitLocker? BitLocker is Microsoft’s full disk encryption solution. While there are alternative solutions from other companies, my experience shows that BitLocker is the preferred choice for most organizations today. The reasons are straightforward: it’s included at no additional cost and integrates seamlessly with Active Directory and EntraID.
This article will guide you through setting up BitLocker and also go into some of the potential attacks against BitLocker, offering insights into its security features.
Table of Contents
First check: I am using BitLocker?
Determining whether you’re using BitLocker is straightforward. Simply open This PC in File Explorer, where you’ll see your drives listed. If your drives display a little lock symbol, as shown in the figure below, then BitLocker should be active on your system. However, don’t stop reading just yet—it’s not quite that simple.

You can also verify BitLocker’s status through the Control Panel by navigating to BitLocker Drive Encryption/Manager BitLocker.
Alternatively, use this PowerShell command:
(New-Object -ComObject Shell.Application).NameSpace('C:').Self.ExtendedProperty('System.Volume.BitLockerProtection')
A result of 1 indicates that the drive is Encrypted.
But why is it crucial to have BitLocker enabled? Without it, anyone with physical access to your computer, such as a thief, could easily remove the hard drive and access its data. Another method to access your data is by booting the computer from a USB drive and reading the disk contents directly.
To illustrate how simple this attack can be, I’ve created a short video:
If your drive is not encrypted, you should take immediate action. This involves either enabling BitLocker yourself or consulting with your system administrators about it.
Enabling BitLocker
Activating BitLocker on a machine you manage yourself is relatively straightforward. Simply navigate to BitLocker Drive Encryption in the Control Panel and click on “Enable.” The wizard that follows is intuitive. It’s very important that in the end you securely back up your recovery key.
The most efficient method I’ve found is to print the key to a PDF and then securely store it. Considering BitLocker’s system integrity checks, this recovery key becomes indispensable. Such checks could trigger a lockout upon updates to your BIOS/UEFI or changes in hardware configuration. Hence, keeping this key in a secure location, such as a password manager, is crucial for system recovery.
But, Is Your System Fully Secure Now?
By enabling BitLocker without pre-boot authentication, your computer will boot as usual. The TPM chip embedded in your motherboard conducts a verification to ensure your hardware has not been altered and that the system booting is indeed your Windows. If this verification is successful, it releases the encryption keys, allowing Windows to decrypt your data without the need for a password (aside from your Windows login password).
This process, while seemingly magical, is a robust security measure. It effectively prevents attackers from utilizing your hard drive on another PC or booting from an alternative operating system.
So, are we done now? Sadly not yet. There are still several possible attacks. For those interested in understanding these vulnerabilities from the perspective of an attacker, the following videos detail these attacks comprehensively.
Cold Boot Attack
Attack on the TPM itself
Direct Memory Access
Some Mitigations
To enhance your system’s security, consider applying the following additional settings:
Kernel DMA Protection
Thunderbolt-connected devices have the capability to perform direct memory access (DMA), posing a risk that an attacker could manipulate memory directly to bypass the logon screen, even if it’s locked.
To mitigate this risk, it’s recommended to enable Kernel DMA Protection. This setting ensures that unknown devices can only be connected when the screen is unlocked, thereby preventing attackers from exploiting this vulnerability to circumvent the lock screen.
Enabling this feature requires activating virtualization technology in your BIOS/UEFI, typically referred to as Intel VT-d or AMD VT-d.
You can verify if Kernel DMA Protection is enabled on your system by running msinfo32.exe and checking for the Kernel DMA Protection entry, which should be set to On.
Virtualization Based Security (VBS)
While Kernel DMA Protection offers a safeguard against Thunderbolt devices, it does not extend protection to potential attacks through PCI Express devices. Even if your laptop lacks a PCI Express slot, it likely includes an M.2 slot, which could be exploited for direct memory access. Further details on Direct Memory Access attacks are available in the video mentioned above.
To defend against these and other sophisticated attacks, enabling Virtualization Based Security (VBS) is recommended. The activation process mirrors that of Kernel DMA Protection, requiring the enabling of virtualization technology in your BIOS/UEFI settings.
The status of VBS can be verified by running msinfo32.exe just as with Kernel DMA Protection.
BIOS/UEFI Password
Implementing the above security measures necessitates hardware support, which can be easily disabled through the BIOS/UEFI settings. To prevent unauthorized alterations, setting a BIOS/UEFI password is crucial. This ensures that the enhanced security configurations remain intact and protected from tampering.
Pre-Boot Authentication
While the features discussed previously are valuable and should be enabled, they only augment a solution that isn’t perfect on its own. BitLocker, when set up without pre-boot authentication, offers superb user-friendliness and is likely sufficient for the average user. Indeed, this is my go-to setup for friends and family. However, for machines handling sensitive information, pre-boot authentication is indispensable. I am not aware of any method to bypass pre-boot authentication, so if a device equipped with it is stolen, the data remains secure. Unfortunately, enabling it isn’t straightforward. Let me guide you through the process.
Enabling pre-boot authentication via the user interface directly is not possible to my knowledge. Instead, group policies must be edited. On self-managed machines, open gpedit.msc (use Windows + R). Navigate to the following path:
Computer Configuration ->
Administrative Templates ->
Windows Components ->
BitLocker Drive Encryption ->
Operating System Drives
Settings to Configure
Require Additional Authentication at Startup
Ensure Allow BitLocker without a compatible TPM is disabled. BitLocker’s full potential is unlocked with a TPM, which is present in almost all modern computers. Although BitLocker can function without a TPM, its security features are significantly reduced.
Set Configure TPM startup PIN to required. This mandates (and actually allows) the use of pre boot authentication.
Allow Enhanced PINs for Startup
Enable this setting to allow PINs that include characters beyond numbers, enhancing the complexity and security of your PIN.
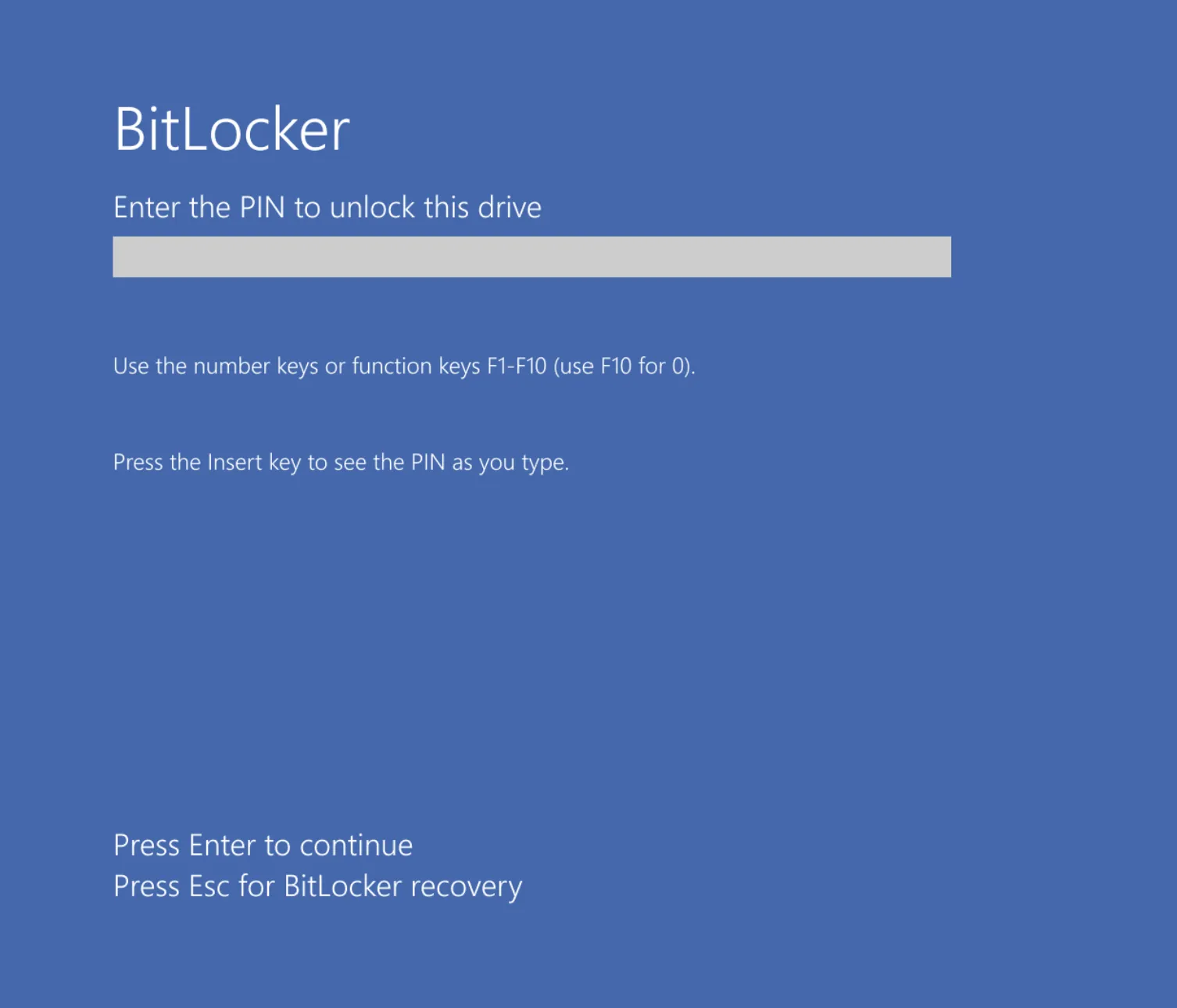
Enabling Pre-Boot Authentication
This part can be a bit tricky. While there are methods to change the authentication mode, I’ve found that the simplest approach is to disable and then re-enable BitLocker via the GUI (search for Manage BitLocker in the start menu). Upon reactivation, you should be prompted to create a PIN. Remember, this action changes your recovery key. Securely store the new recovery key and appropriately dispose of or mark the old one as obsolete.
Congratulations, your device is now secured with BitLocker and pre-boot authentication!
Summary
To wrap up this comprehensive guide, here are the key security measures you should implement:
- Activate BitLocker for disk encryption.
- Use pre-boot authentication on devices handling sensitive information.
- Set a BIOS/UEFI password to secure your hardware settings.
- Enable Virtualization Based Security for enhanced protection.
While it may seem daunting, these steps are straightforward and significantly bolster your Windows security.
|
martin@vidrasec.com |
+43 670 3081275 |
+43 670 3081275 |
Book appointment |