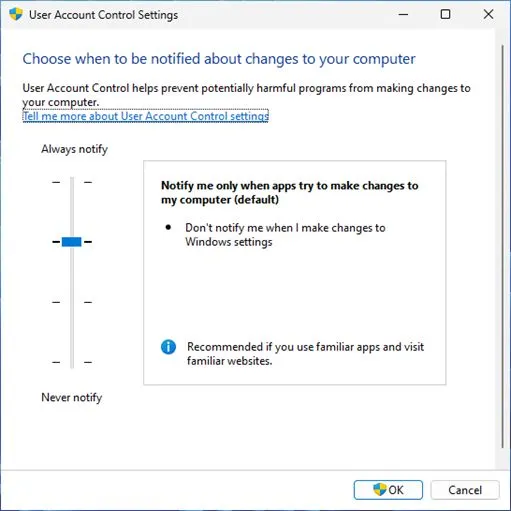
What do we see in the photo? The settings for User Account Control (UAC). But what exactly is that and how can it be bypassed?
UAC is an important security feature that was introduced with Windows Vista. Even if you have local admin rights, applications by default run with restricted rights. If admin rights are needed, the program must be manually started as an admin. This concept is called “Mandatory Integrity Control” or “Integrity Levels.”
What are the IT security implications of this? If I accidentally run malware, it will only have limited rights. Still bad, but better. Therefore, this is an important security feature and should always be active.
The problem in the screenshot: The default UAC setting in the screenshot does not require confirmation for changes to Windows settings. At first glance, this might seem fine, but it is not.
If the slider is set to this level, UAC can be easily bypassed and a program can easily gain admin rights. Microsoft does not consider UAC a security boundary, so the vulnerability will not be fixed.
Okay, what is the countermeasure? Fortunately, it’s simple: the slider should always be set to the highest level, “Always Notify.” However, this setting can also be bypassed. Therefore, UAC is not a true security measure, but in my opinion, it can still protect against some attackers.
Much more important: Especially in the corporate environment, I should never work with local admin rights. Still, I always recommend setting the slider to the highest level via Group Policy because there are often 1-2 exceptions who have local admin rights.
Below is a video of the exploit:
Contact
For further questions about Windows security, feel free to contact VidraSec.
|
+43 720 971425 |
martin@vidrasec.com |
Book appointment |