What is a penetration test?
How secure are your IT systems really? A penetration test shows where attackers would start - before it’s too late
A penetration test (“pentest” for short) is a security analysis of one or more IT systems. An IT security expert (“pentester”) attempts to uncover as many vulnerabilities as possible in the time available. The tools and procedures used are the same as those used by real attackers. The result of a penetration test is a detailed report with the vulnerabilities found, sorted by severity, and recommended measures to eliminate them.
Why penetration testing?
- Every system has unknown vulnerabilities.
- Without testing, they remain undiscovered until an attacker exploits them.
- Penetration tests find these vulnerabilities
- So that they can be fixed before attackers exploit them
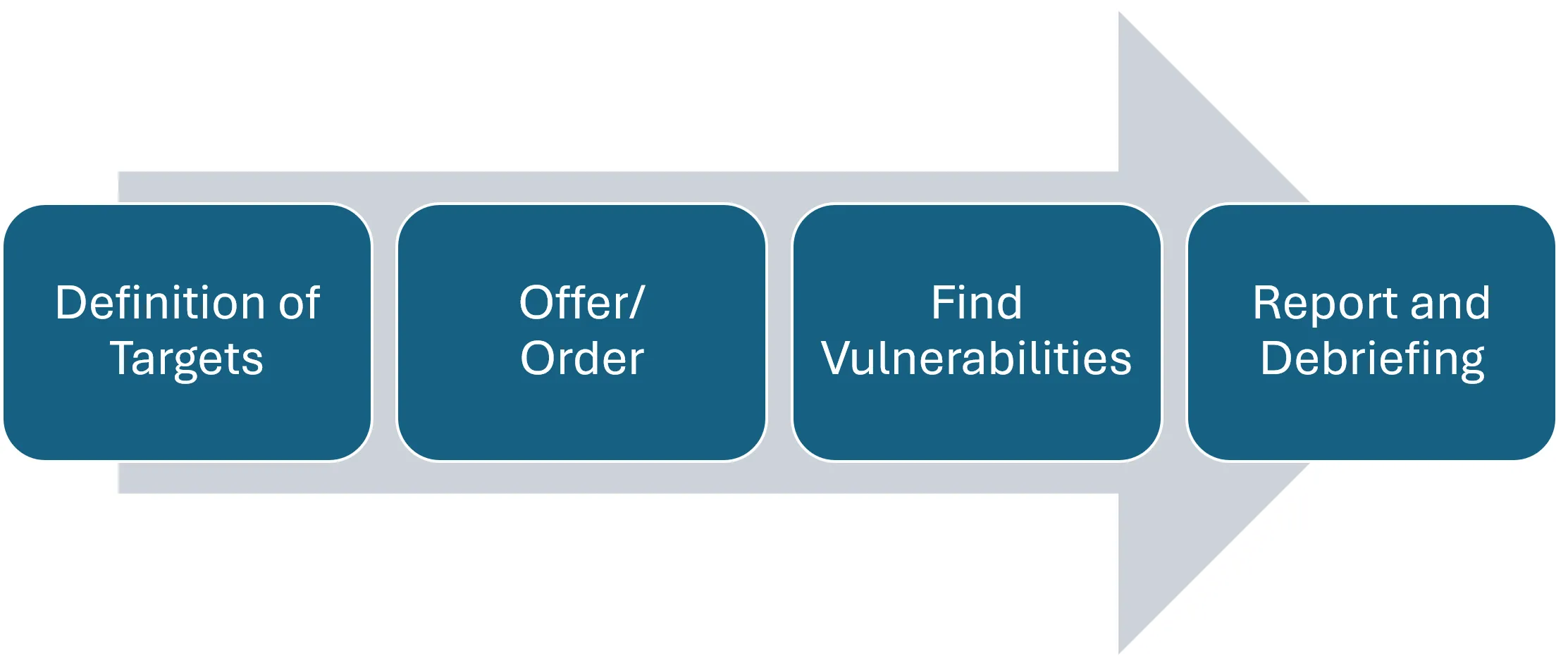
Penetration test procedure
Commercial details
- Penetration tests are always customized to the tested systems and requirements - there is no standard price.
- Implementation in a time box: How many vulnerabilities can be found in the time available?
A cyber attack is expensive! Take precautions now and sleep better at night!
Typical price: from €5,600.00 (for 3 days test + documentation)
Specific services
Every IT system is different. A penetration test of the internal IT infrastructure, for example, requires a completely different approach and tools than a penetration test of a web application.
Ransomware attacks are on the rise, and the ones with the highest impact take over the whole Active Directory. We must secure these systems to minimize the risk of having our data encrypted and put up for sale on the internet!
What if one of your employees clicks on the wrong email attachment? Will you be able to stop the attack, or will the attackers be able to move laterally from there and take over all your systems? This is why you should conduct an internal infrastructure penetration test. The internal system is just one wrong click away from being “public”.

Cloud services offer many new opportunities for companies. However, they also present many dangers that can be exploited by attackers. Therefore, it is essential that these services are configured correctly. This configuration is checked in a Cloud Infrastructure Audit.

EntraID is a very powerful identity management and access control solution. A misconfiguration can lead to unauthorized access to company resources or facilitate social engineering attacks. Therefore, this component must be thoroughly tested.
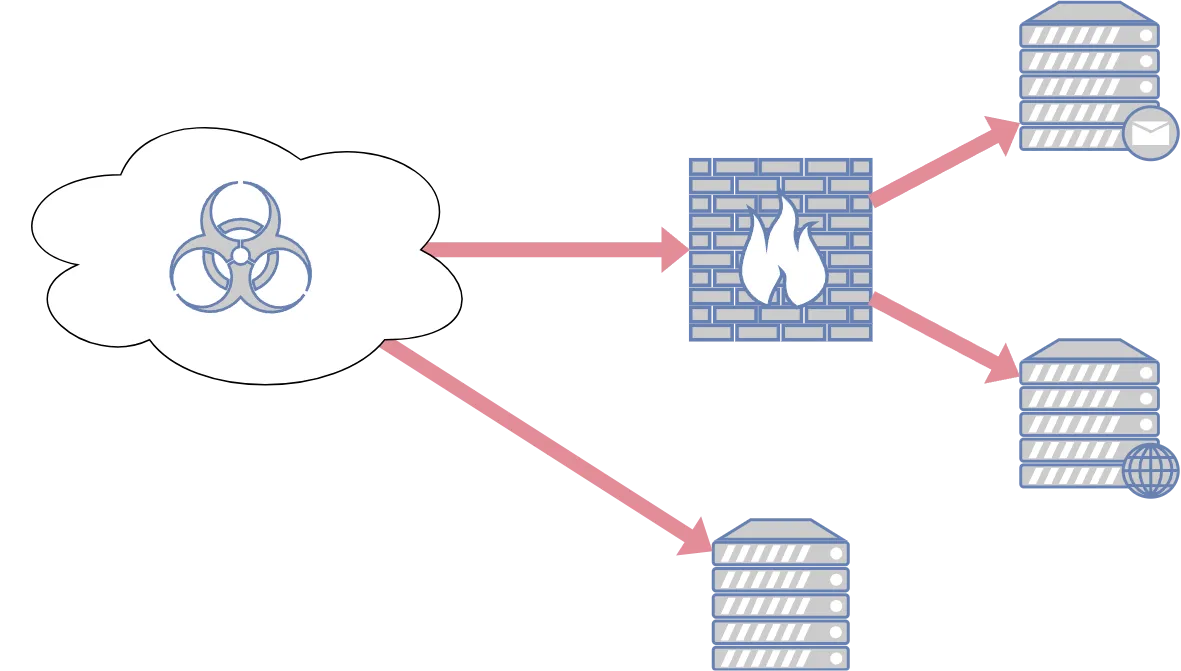
If your system is exposed to the internet, it could potentially be hacked by anyone. Okay, I exaggerate a bit, but I think you understand. Vulnerabilities in your external infrastructure can lead to very bad press and threaten your customers’ personal information. So, it’s better to check once more.
Vulnerabilities in web applications can be very problematic. In the worst case, the entire web server is taken over or confidential customer data is stolen. Therefore, it is especially important to thoroughly test these applications.






