Internal IT Infrastructure Penetration Test
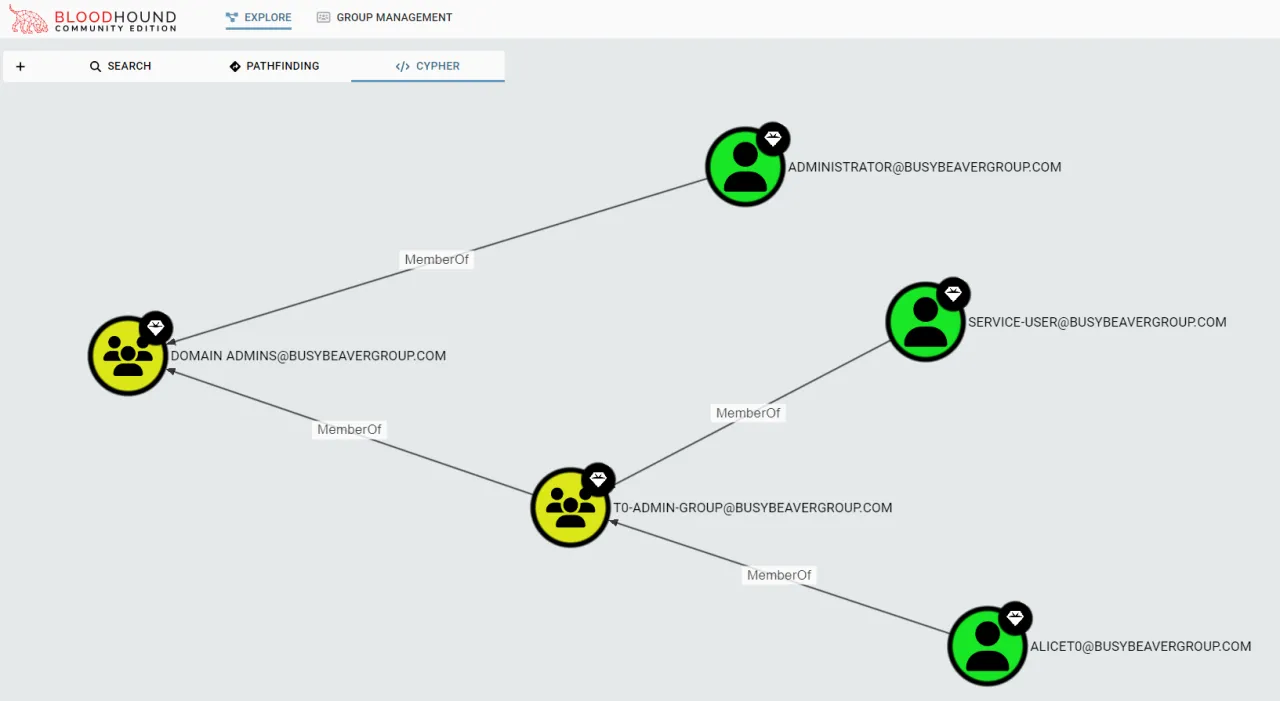
What if one of your employees clicks on the wrong email attachment? Will you be able to stop the attack, or will the attackers be able to move laterally from there and take over all your systems? This is why you should conduct an internal infrastructure penetration test. The internal system is just one wrong click away from being “public”.