Active Directory Audit
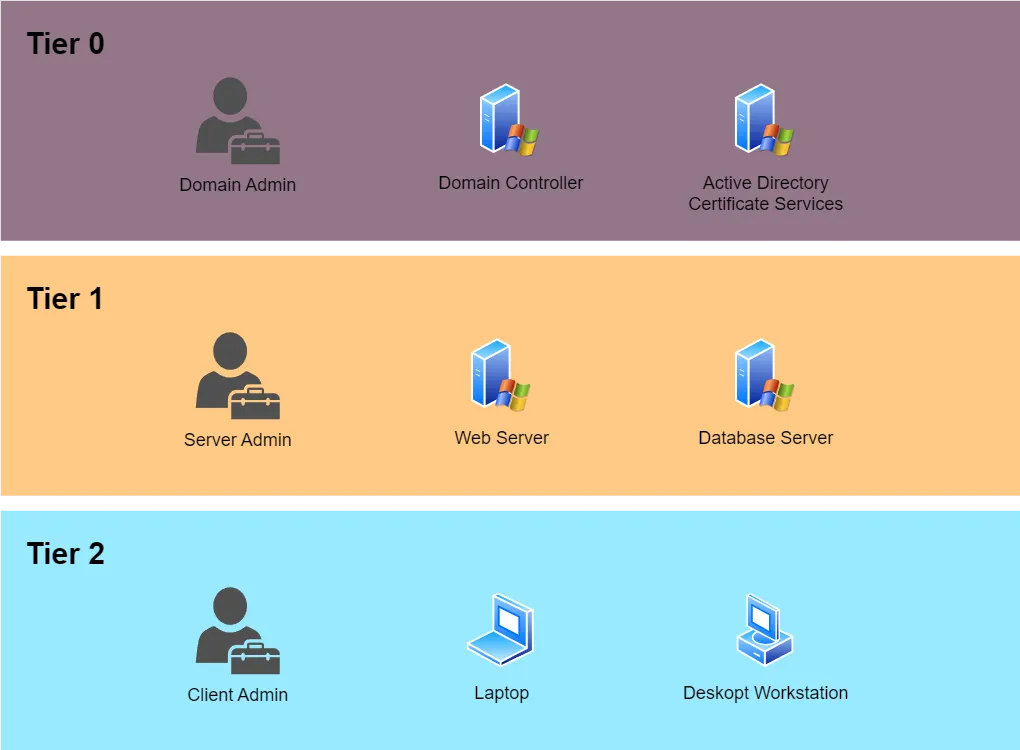
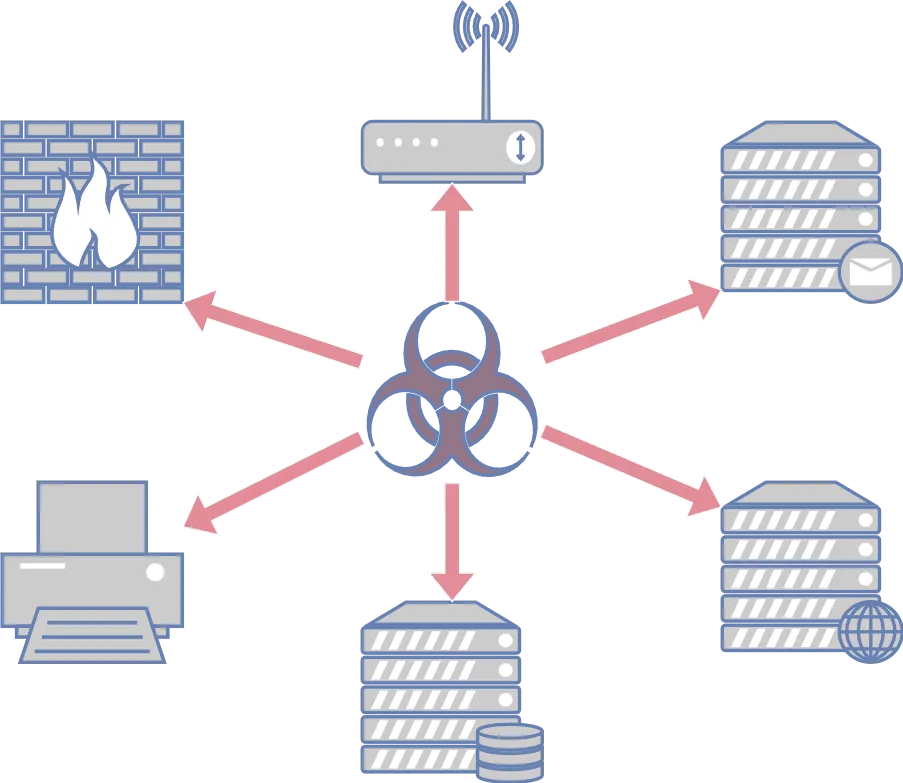
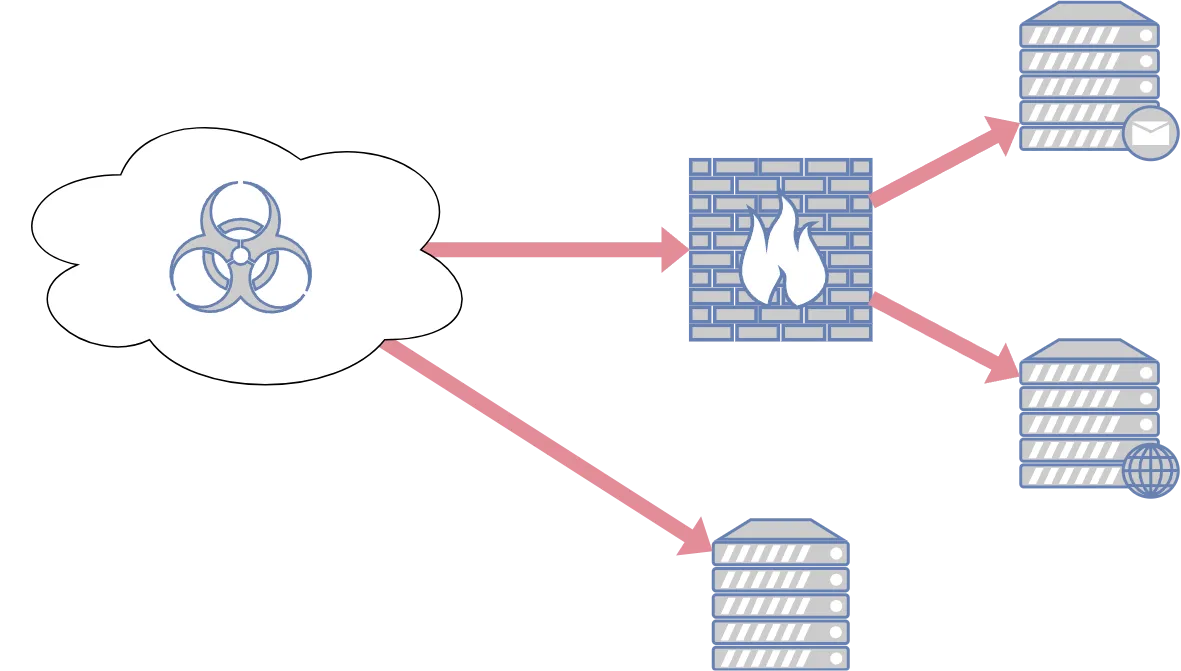
Ransomware attacks are on the rise, and the ones with the highest impact take over the whole Active Directory. We must secure these systems to minimize the risk of having our data encrypted and put up for sale on the internet!